Security researcher James Kettle digs deep into the web stack to reveal some shiny new attack surface

HTTP/2 specification pitfalls and implementation errors have resulted in some of the world’s biggest tech companies exposing themselves to high-impact web attacks, new research shows.
Two years after taking to the Black Hat USA stage to document his exploits in the field of HTTP request smuggling, PortSwigger* security researcher James Kettle is back with a fresh perspective into how this attack vector can also impact HTTP/2 infrastructure.
RELATED Black Hat 2021: Zero-days, ransoms, supply chains, oh my!
The results are enough to keep sysadmins awake at night, as the researcher demonstrated how desynchronization attacks levied against HTTP/2 systems enabled him to steal secrets from websites running Amazon’s Application Load Balancer, poison every page on Bitbucket, and forced Atlassian to sign every single one of its users out of Jira.
Request smuggling redux
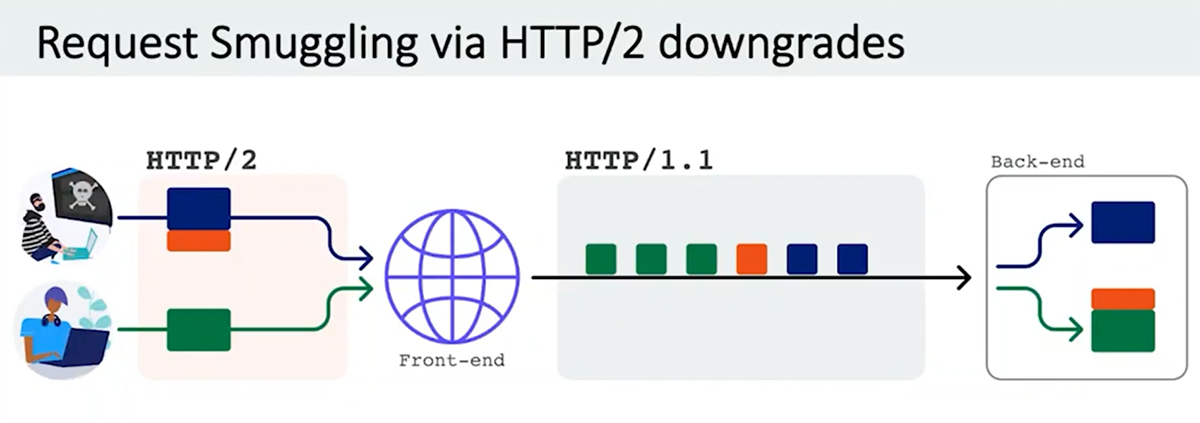
Traditional request smuggling uses HTTP header manipulation to send requests in such a way that the backend and frontend systems think the request is a different length.
Through splitting the request, an attacker can force servers and clients to spit out reams of secrets, including user data and private keys.
BACKGROUND Ancient technique tears a hole through modern web stacks at Black Hat 2019
HTTP/2 includes several performance and security advantages over HTTP/1.1. The binary protocol design that replaces HTTP’s plaintext design can help stamp out request smuggling as an attack vector.
“HTTP/1 relies on the user sending their Content-Length, or a Transfer-Encoding: chunked header, in order to tell the server what the length of the message is,” Kettle explained during his talk at Black Hat USA today (August 5).
“HTTP/2 doesn’t require either of these headers. Instead, the length is built into the frame layer. As a result, it’s impossible to send an HTTP/2 message that is ambiguous about what its length is.”
HTTP/2 request smuggling – how is it possible?
Given the protocol improvements, one might ask how it is possible to conduct request smuggling attacks with HTTP/2 infrastructure. According to Kettle, the answer stems from the well-worn adage of complexity being the enemy of security.
The researcher explained: “Why is HTTP/2 request smuggling possible? Unfortunately, the majority of servers that speak HTTP/2 to the client actually rewrite requests as HTTP/1 in order to talk to the backend server.
This behaviour is “ridiculously common”, Kettle said, who added that Amazon’s application load balancer was among the many offending web services.
 Request smuggling can force servers and clients to leak secrets
Request smuggling can force servers and clients to leak secrets
This approach – which Kettle calls ‘HTTP/2 downgrading’ – effectively removes all the security benefits that administrators should be getting from using HTTP/2.
Attacks in action
In a technical white paper, HTTP/2: The Sequel is Always Worse, released in tandem with his Black Hat presentation today, Kettle explained how HTTP/2 downgrading attacks enabled him to scoop a $20,000 bug bounty from Netflix.
“Netflix was using the Netty Java library for their HTTP/2 support and that library forgot to verify that the Content-Length was correct,” he said.
By exploiting this flaw, an attacker could redirect users to their own website, achieve persistent JavaScript execution on Netflix’s core website, or hijack user accounts en masse.
Read more about the latest hacking techniques
The attacks don’t end here: After discovering that AWS’ Application Load Balancer was downgrading connections, Kettle said he could conduct request smuggling attacks on every site that used the load balancer, including a law enforcement portal.
Among his other victims was the Incapsula WAF, (web application firewall) the Netlify content delivery network, and Atlassian’s Jira, the latter of which forced a global user sign-out in order to ensure the issue had been mitigated.
Also of note was an attack against Bitbucket. The DevOps tool had proved a difficult target for Kettle’s previous exploits, but further research resulted in him being able to take control of every page on the Bitbucket website.
 James Kettle presented his latest request smuggling research at Black Hat USA 2021
James Kettle presented his latest request smuggling research at Black Hat USA 2021
Securing the stack
In a world where HTTP/2 is spoken consistently by all systems, most of these request smuggling attacks would fail. In reality, we still have a long way to go.
According to W3techs, HTTP/2 is currently supported by just 46% of all websites – and it is not known how many of these conduct downgrading behind the scenes.
RELATED H2C smuggling named top web hacking technique of 2020
“If you take your frontend server, turn on HTTP/2 support and do downgrading, congratulations: you have just doubled the number of ways that you may be vulnerable to request smuggling,” Kettle warns.
As part of his research, Kettle has released an open source tool to help security teams test their own systems for HTTP/2 request smuggling flaws.
“The simplest way to avoid these problems on your website is to avoid downgrading,” he told The Daily Swig. “Leave HTTP/2 switched off until you can support it end to end.
“HTTP/2 is a beautiful beast, but it is complex – and where there’s complexity, people take shortcuts and things go wrong.”* PortSwigger Web Security is The Daily Swig’s parent company.
INTERVIEW Aaron Portnoy – ‘There’s no silver bullet for ransomware or supply chain attacks’






