Putting the ‘bee’ in BSides

BSides Manchester opened its doors in the UK’s second city yesterday, offering a community-focused program of talks, workshops, and hacker challenges.
One of the more important dates in Britain’s cybersecurity calendar, BSides Manchester, now in its sixth edition, boasted more than 600 people this year – a new turnout record, according to its organizers.
“Every year we seem to attract more people, and from more diverse backgrounds as well, which is brilliant,” said organizing committee member, Matt Summers.
“So not just from traditional security,” he added. “A lot of people from test functions and development functions are here today.”
With four tracks packed with presentations offering a mix of technical and socially-oriented topics, the conference didn’t fail to deliver on leaving its attendees inspired, beginning the night before at its traditional ‘BeerSides’ meetup.
Held in the upstairs room of a nearby bar on Wednesday evening, the event offered security pros a chance to see old friends and make new contacts ahead of the main event.
Four lightning talks were also presented, including one highlighting how social networking apps for pet owners were so insecure they might pose a stalking risk to their owners by David Lodge of Pen Test Partners.
The presentations
PortSwigger’s own James Kettle kicked off the morning talks on Track One with his presentation of HTTP request smuggling – an ancient web hacking technique that he’s revamped to break into systems like PayPal and Red Hat.
“We tell people things like ‘HTTP is stateless’ and ‘If you send one request, you get one response’, but what if both of those were kind of wrong,” Kettle told The Daily Swig earlier this month, explaining how he was able to poison web caches and desynchronize entire systems due to security shortfalls of the HTTP protocol.
“The most vulnerable system is one that has lots of proxies, lots of layers, and caches, things like that,” Kettle said. The security researcher bagged more than $70,000 in bounties for his findings.
 Request smuggler James Kettle
Request smuggler James Kettle
Attendees had plenty of talks to choose from, and – despite the BeerSides partying the night before – the alternate morning session tracks were brimming with people lining up to see Gavin Johnson-Lynn detail his journey from software developer to red teamer, Brett Calderbank teach the benefits of monitoring files with FIM, and Rachael Stos-Gale discuss how to recruit the right people for entry-level security roles.

Several of the talks at BSides Manchester 2019 offered practical advice from experts in a particular field rather than fresh research. A good example of this was Derek Price’s talk on Microsoft’s Enhanced Security Administration (ESA), also known as the ‘Red Forest’.
The technology, which has been around for some years but has only recently been more actively promoted, offers a protected platform to manage enterprise-wide Active Directory deployments.
Price’s talk covered the architecture and logistics of building the Red Forest, as well as the practical problems he’s encountered in projects involving rolling out the technology.
 Going phishing overboard with Elise Manna
Going phishing overboard with Elise Manna
And for all things phishing, delegates headed over to the Rookie track to hear Elise Manna, a director of threat operations, go “phishing overboard”.
Manna took participants through various phishing techniques – credential harvesters rather than anything that drops a payload – explaining how they manage to evade detection and continue to end up in users’ inboxes.
“It’s been frustrating because you see the same things working over and over again and nobody seems to be doing anything about it,” she said.
“It gives me a little bit of a reason to drink whisky sometimes.”
Sticking with phishing, Charlie Hosier, a soon to be junior cybersecurity consultant at NCC Group, took participants through the Open Graph protocol, a tool for enhancing web pages.
Hoiser explained that the meta tags used as part of the protocol can be manipulated by attackers to redirect users to malicious web pages.
“The Open Graph protocol works across platform, as well,” he said.
“The problem with this is that these Open Graph objects generate server side, which means that a user assumes that the object has been generated by the application and is therefore more likely to trust that link.”
Analogies with technologies like predictive texting and comparisons with sci-fi blockbuster Minority Report took center stage in a presentation from security researcher and software developer James Stevenson, entitled ‘Profiling the Attacker – Using Natural Language Processing to Predict Crime’.
The talk outlined how machine learning – specifically, natural language processing and sentiment analysis – is already being used by the police in attempts to predict crime.
Similar approaches might be used in attempts to predict future security attacks by applying a novel ways of analyzing security logs.
Natural language processing can be used to automate this whole process, according to Stevenson, who is working on a PhD based on the concept.
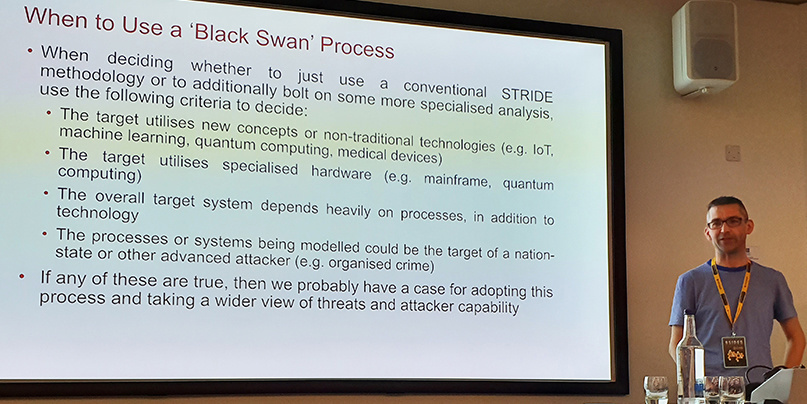
Hacker Nick Dunn kicked off the afternoon sessions by providing an outline of ‘Black Swan’, a threat modelling methodology for non-standard systems and apps.
“If the target utilizes particularly new concepts or non-traditional technologies – such as medical devices, machine learning, or specialized hardware – then you’ve probably got a reasonable case for doing the STRIDE process in the normal way, but then stepping outside and taking a look at what else could go wrong,” he said.
Dunn said he will post full details of the Black Swan method over the coming days.
 Nick Dunn: White Hats and Black Swans
Nick Dunn: White Hats and Black Swans
BlackBerry threat analyst Alex Burrage discussed the security considerations that can influence an organization’s decision to adopt (or remove) open source software.
Burrage shared his seven-step guide for assessing risk in open source projects and libraries. This takes into account numerous factors, including the size of the development team, quality of documentation, and frequency of updates.
The analyst closed his talk with a light-hearted request for someone to develop a tool that would allow security staffers to automatically assess risk factors in open source libraries.
Of course, if someone were to build such a project, it would only make sense for this to be open-sourced, too...
Are you in the infosec echo chamber? James Carter urged security pros to ensure they are speaking the right language to colleagues in order to get their voices heard.
“As security professionals, we use a really specific language,” he said. “We talk about zero-days, vulnerabilities, malware, and all the other things that are incredibly important to how we do our jobs. But that’s not the language that our organizations speak.”
In a highly entertaining talk, Netacea’s James Maude provided a lightning-fast tour of the bot ecosystem and how these automated (and often legal) threats are giving organizations no shortage of headaches.
“In retail and travel, specifically, nine out of 10 login attempts, in the sites that I’ve been looking at from March to July, have been from automated credential stuffing or account takeover systems,” he said.
“That’s a huge amount of traffic, and a huge amount of resources [being used] to feed things and give information back that, potentially, you don’t want. That’s not a real customer, that’s someone else trying to trick a system.”
And fellow security researcher and northerner Scott Helme helped finish off the day with a practical look at the tools available to help monitor web browser security, including how to utilize error reports, a new feature from Google Chrome.
Helme took BSides attendees through the wide-range of data that could be made available to researchers to help determine what is going wrong with a website.
“I would love the browser to tell me that I’ve got an expired certificate, or invalid cert, or I’ve screwed something up, tell me, and these are all the types of things that you can subscribe to,” Helme said.
 Crash, Burn, Report
Crash, Burn, Report
Those interested in catching up on all of the sessions should keep a close eye on the BSides Manchester YouTube channel.
Off-piste
Outside the talks themselves, BSides Manchester participants enjoyed the chance to brush up on their lock-picking skills, collect swag, and trade stickers.
Alongside this, community groups OWASP, Manchester Grey Hats, and InfoSec Hoppers were out in full force, raising a spanking £1,000 ($1,200) for UK mental health charity, Mind.
 Sticker swag at BSides Manchester
Sticker swag at BSides Manchester
“I think it’s the community feel,” Summers said of BSides Manchester’s ongoing success.
“There’s a lot of local people that bring so much, and I keep saying this, but they’re not [all] from a security background. They’re developers, testers, and it feels like everyone knows everyone.”
 Until next year...
Until next year...
Additional reporting by John Leyden and James Walker






