Tech giant hails a ‘record-breaking year’ for vulnerability disclosure programs

Google has praised security researchers in what the tech giant has called a “record-breaking year” for its vulnerability reward programs.
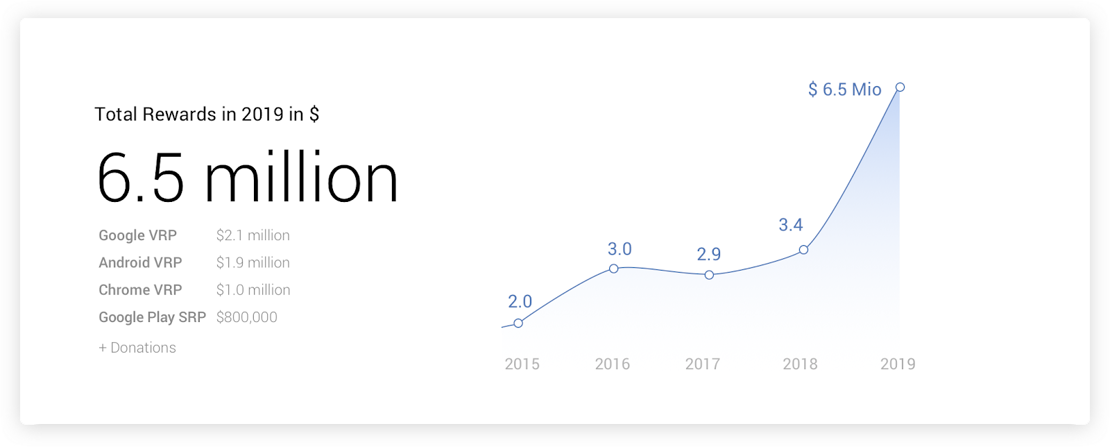
In a blog post penned yesterday (January 28), Mountain View announced that it had paid out over $6.5 million in bug bounties in 2019 – doubling the amount it allocated to awards in any other year.
“Our Vulnerability Reward Programs were created to reward researchers for protecting users by telling us about the security bugs they find,” Google said.
“Their discoveries help keep our users, and the internet at large, safe.”
Google has long cemented itself in the security community, having implemented its take on bug bounties through its Vulnerability Reward Programs (VRPs) since 2010.
In 2014, before the tech giant opened up its reward scheme to include scopes such as Google Play, Google Drive, and Android, the company had paid out an accumulated total of $4 million to researchers.
Fast-forward to 2019, and Google has amounted a grand total of $21 million paid in rewards – an accomplishment it pegs on the combination of new programs and higher bounties.
The biggest single bug bounty payout in 2019 was $201,000.
Read the latest bug bounty and security news
“Since 2010, we have expanded our VRPs to cover additional Google product areas, including Chrome, Android, and most recently Abuse,” the company said.
“We’ve also expanded to cover popular third-party apps on Google Play, helping identify and disclose vulnerabilities to impacted app developers.”
Specific changes to Google’s VRPs have included tripling the maximum baseline reward amount for vulnerabilities found in Chrome – from $5,000 to $15,000 – and upping the ante to $30,000 for high quality reports.
 Google handed out more than $6.5 million in bug bounties in 2019
Google handed out more than $6.5 million in bug bounties in 2019
The Android Security Rewards Program, created in 2015, equally saw a widening of exploit categories with higher payouts.
“The top prize is now $1 million for a full chain remote code execution exploit with persistence which compromises the Titan M secure element on Pixel devices,” Google said.
“And if you achieve that exploit on specific developer preview versions of Android, we’re adding in a 50% bonus, making the top prize $1.5 million.”
Sticking with the Android ecosystem, Google launched the Developer Data Protection Reward Program in 2019 to help deal with issues related to apps, additionally expanding its Google Play Security Reward Program to offer payouts to issues found in apps with over 100 million installations.
This resulted in “over $650,000 in rewards in the second half of 2019”, the tech giant said.
Google also praised its own security researchers, who donated a total of $500,000 to charity in 2019 off the back of their bug findings.
See the full list of vulnerability targets and research via Google Security Reward Programs.
RELATED Project Zero relaxes 90-day vulnerability disclosure deadline to boost patch adoption






