Exploit allows potentially malicious content to bypass browser’s defenses

UPDATE (Oct 23; 16:25 UTC) This issue has been patched in Firefox 70. See our coverage for more details.
A technique to evade Content Security Policy (CSP) leaves surfers using the latest version of Firefox vulnerable to cross-site scripting (XSS) exploits.
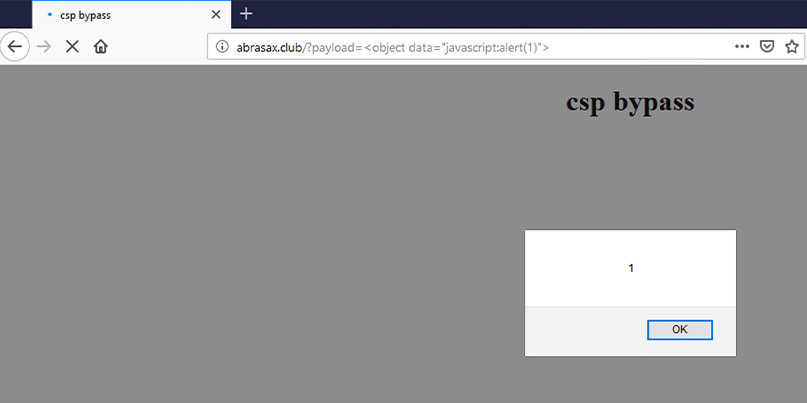
Researcher Matheus Vrech uncovered a full-blown CSP bypass in the latest version of Mozilla’s open source web browser that relies on using an object tag attached to a data attribute that points to a JavaScript URL.
The trick allows potentially malicious content to bypass the CSP directive that would normally prevent such objects from being loaded.
Vrech developed proof-of-concept code that shows the trick working in the current version of Firefox (version 69).
The Daily Swig was able to confirm that the exploit worked.
The latest beta versions of Firefox are not vulnerable, as Vrech notes. Chrome, Safari, and Edge are unaffected.
If left unaddressed, the bug could make it easier to execute certain XSS attacks that would otherwise be foiled by CSP.
The Daily Swig has invited Mozilla to comment on Vrech’s find, which he is hoping will earn recognition under the software developer’s bug bounty program.
The researcher told The Daily Swig about how he came across the vulnerability.
“I was playing ctf [capture the flag] trying to bypass a CSP without object-src CSP rule and testing some payloads I found this non intended (by anyone) way,” he explained.
“About the impact: everyone that was stuck in a bug bounty XSS due to CSP restrictions should have reported it by this time.”
Content Security Policy is a technology set by websites and used by browsers that can block external resources and prevent XSS attacks.
PortSwigger researcher Gareth Heyes discussed this and other aspect of browser security at OWASP’s flagship European event late last month.






