Open source software EventStream contained malicious code

A popular JavaScript library was infected with cryptocurrency-stealing code after maintenance of the open source project was taken over by a malicious actor.
EventStream, a package for Node.js in the npm repository, was discovered last week to have been injected with data-slurping code targeting cryptowallet CoPay.
The repository, which has more than a 170 million downloads, was originally authored by programmer Dominic Tarr.
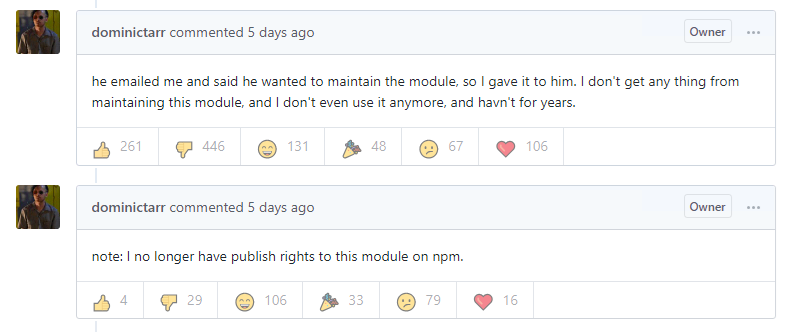
He had been maintaining the library on a voluntarily basis, but gave up his publishing rights and handed control to a user called Right9ctrl.
It was at this point, three months ago, that Right9ctrl released EventStream version 3.3.6, which added a dependency on Flatmap-Stream 0.1.1.
This dependency contained malicious code that activates when it detects CoPay, stealing the users’ private keys and leading some to believe that Right9ctrl was attempting to empty their cryptowallets.
Npm has pulled the dependency from its registry, and fixes are being rolled out.
So far, Right9ctrl has not responded to the accusations that he intentionally injected the malicious code, while Tarr has also been attacked online.
He weighed in on the issue, stating that he has no control over the project and hasn’t maintained it “for years”.
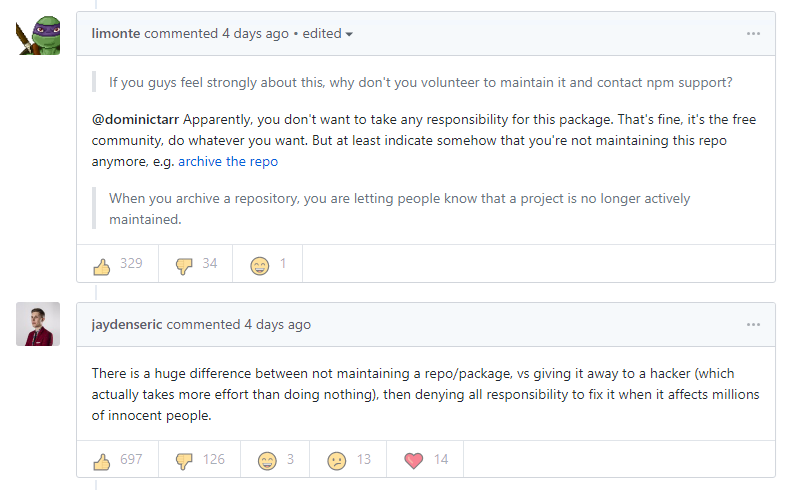
But users have questioned whether he was right to shirk responsibility – especially as his reputation is still attached to it.
Others sided with Tarr, arguing that he was working voluntarily, had given access away in good faith, and therefore wasn’t responsible.
Regardless of where the fault lies, the backdoor discovery once again highlights the inherent security issues that can arise through the use of software dependencies.
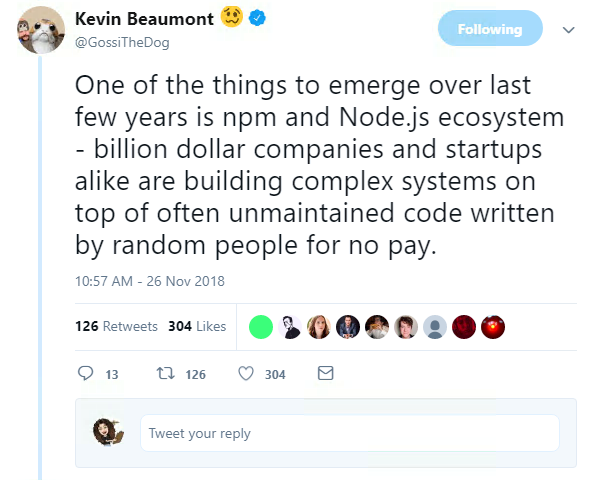
Package managers such as npm for JavaScript contain thousands of packages in their registries, ranging from major libraries built and maintained by a team of trained programmers, to smaller ones written by rookies.
With no overarching authority tasked with ensuring these dependencies are maintained and safe, relying on package managers can create a huge security risk.
Users are giving these libraries full access to their computers – and the time and expertise required to audit dependencies is beyond most developers.
Some have tried to make software dependencies a safer option. Companies promising sanitized versions of package repositories have failed to take off the ground due to a lack of paying customers.
Other projects such as as open source bug bounty program BountyGraph gave companies such as Dropbox the opportunity to pay for its dependencies to be secured, until it announced that it was closing next month.
This once again leaves the question: who will secure the foundations?