Top infosec trends in the social media spotlight

The UK’s data protection laws were once again brought to the fore this month, as the results of an inquiry into Carphone Warehouse circulated around social media.
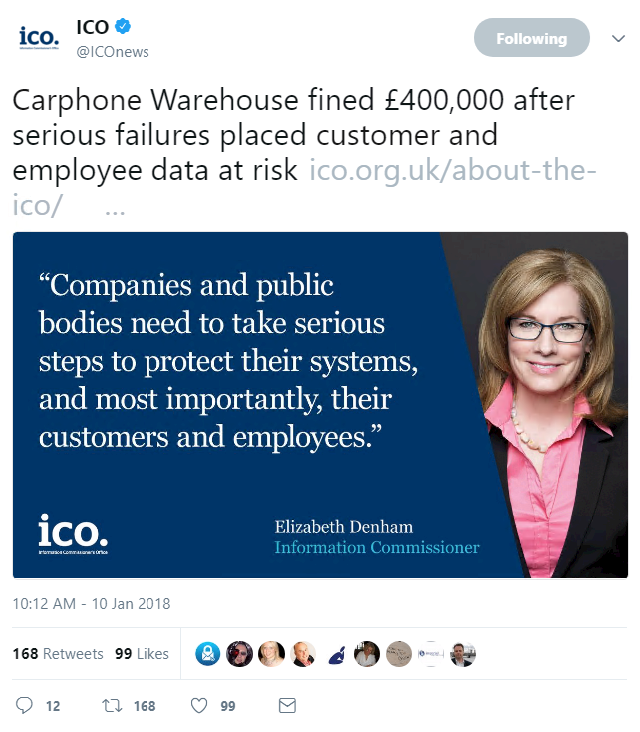
On January 10, the Information Commissioner’s Office (ICO) took to Twitter to announce that the mobile phone retailer would be fined £400,000 ($554,000) after one of the group’s computer systems was hacked in 2015.
Following a detailed investigation, the financial services regulator said it identified multiple inadequacies in Carphone Warehouse’s approach to data security, which led to the personally identifiable information of more than 18,000 customers being compromised.
“Carphone Warehouse should be at the top of its game when it comes to cybersecurity, and it is concerning that the systemic failures we found related to rudimentary, commonplace measures,” said Information Commissioner Elizabeth Denham.
“Outsiders should not be getting to such systems in the first place. Having an effective layered security system will help to mitigate any attack – systems can’t be exploited if intruders can’t get in.”
The £400,000 figure is one of the largest fines ever handed out by the ICO.
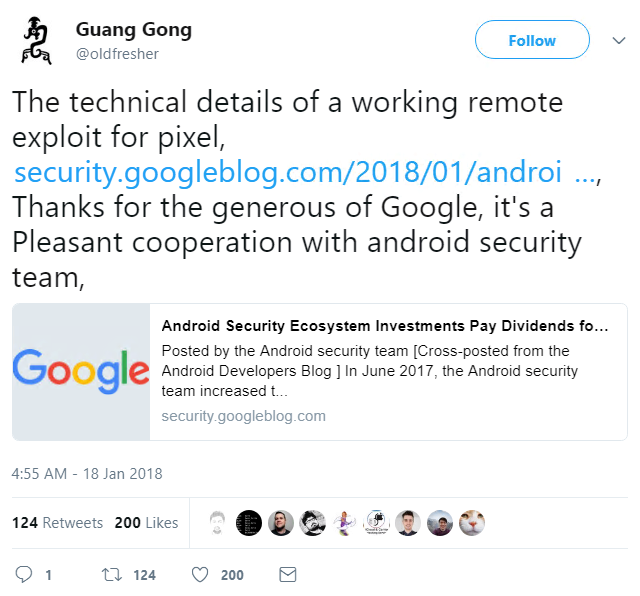
In mobile news, Qihoo 360 researcher Guang Gong has thanked a “generous” Google, after it emerged that he had been awarded a massive $112,500 for identifying two critical vulnerabilities in the Android developer’s popular Pixel device.
While Google’s Pixel handset was the only device that was not hacked at last year’s Mobile Pwn2Own competition, a fresh post on the Google Security Blog provides full details of the vulnerabilities found by Gong, which could be chained for a remote code injection exploit that works against the Android smartphone.
For his detailed report, Gong was awarded a record-breaking $105,000 from the Android Security Rewards program, and a further $7,500 from the Chrome Rewards program. Both issues were patched in December.
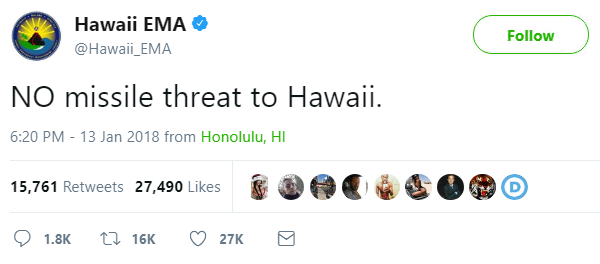
Elsewhere, an incoming missile alert plunged residents of Hawaii into panic on Saturday:
A subsequent statement from the Hawaii Emergency Management Agency (HEMA) described how the warning message sent to all residents’ mobile devices just after 8:00am was triggered by mistake.
Unsurprisingly, the agency’s apologies did little to allay the concerns of the Pacific islanders who frantically sought shelter or sent what they thought might be their last ever messages to loved ones.
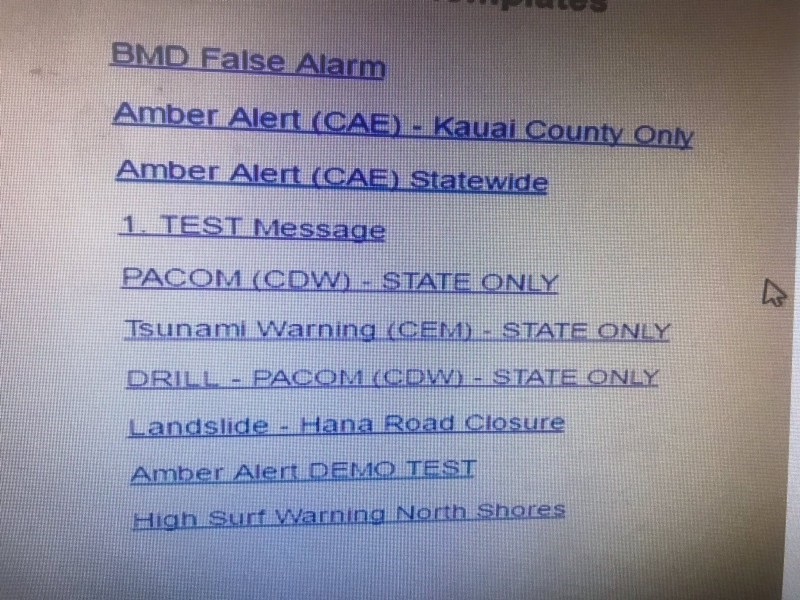
Amid the inevitable fallout from the operational blunder, however, one interesting post on Medium lays the blame not on human error, but on the agency’s poor choice of alert template filenames.
According to the article’s author, Jared Spool, the crux of the error was choosing the wrong file, from a list that looked like this:
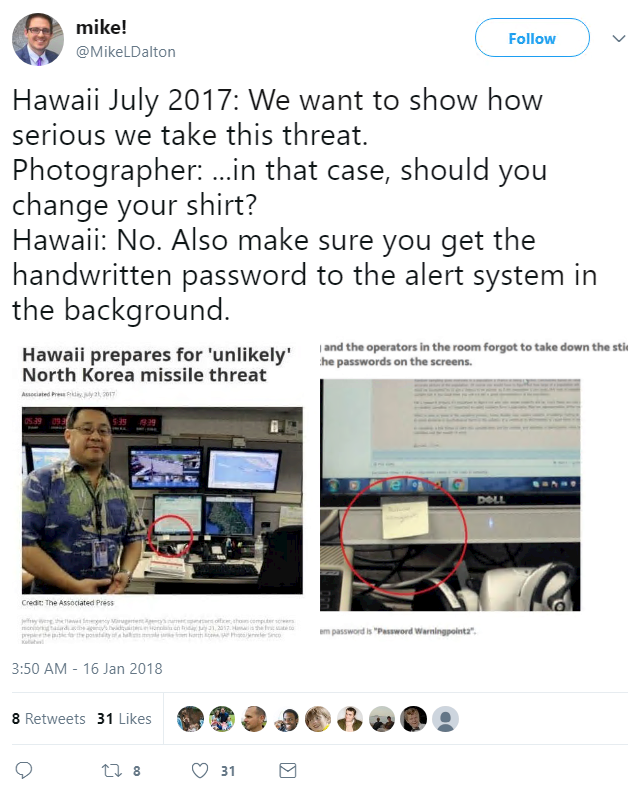
If all this wasn’t enough, a terrible week for HEMA was made even worse when yet another image started doing the rounds on Twitter – this time one that shows an agency officer posing in front of computer screens adorned with post-it notes, one of which spells out a system password.
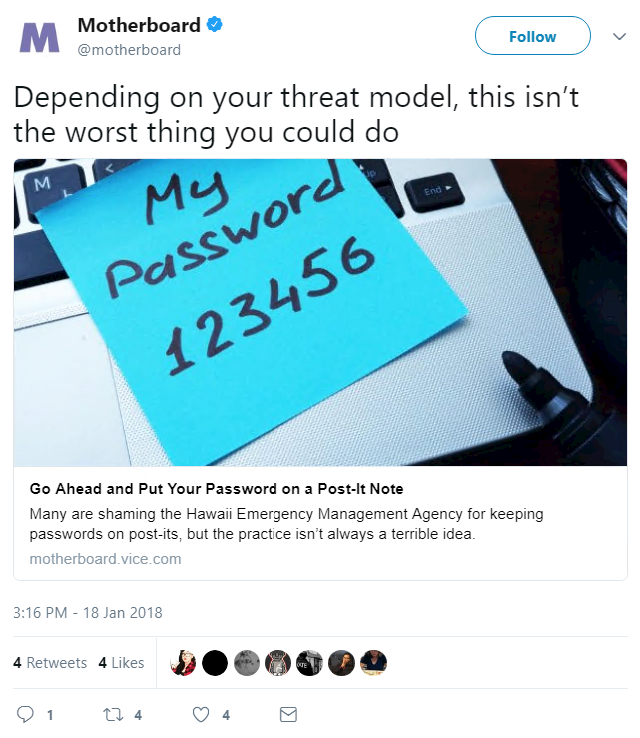
While many were quick to poke fun at the agency’s shoddy security practices, HEMA found an unlikely hero in Motherboard, who launched to its defense with the words: “It’s usually ok to have a password printed on a sticky note.”
“It’s usually OK to have a password printed on a sticky note,” says Motherboard’s Lorenzo Franceschi-Bicchierai.
“Generally speaking, the risk of someone breaking into your home to read that sticky note or notebook is much lower than someone infecting your computer with malware and then accessing all your passwords.”
“In general, we still recommend software password managers. But don’t listen to the security absolutist and tweetshamers who are gloating over what is admittedly a mistake on behalf of HEMA.
“Think about what your threats are, and how to protect against them. That’s how you, and everyone else, will be more secure.”