Tool captures potentially malicious communications being sent from smartphone to WiFi points

A team of security researchers has developed a DIY appliance to detect stalkerware and other malware on smartphones.
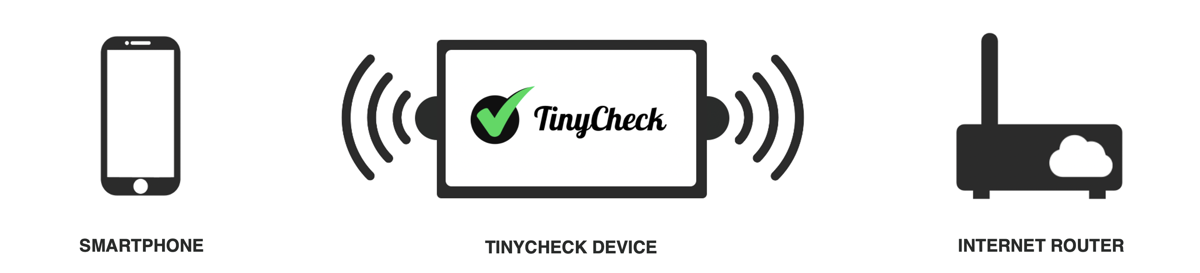
TinyCheck is open source software designed to be used on a Raspberry Pi with WiFi dongle and touchscreen. It was developed by Félix Aimé, a senior security researcher at Kaspersky Lab.
The device monitors traffic between a smartphone and the network to detect signs of stalkerware or other indicators of compromise (IOC) from malicious applications.
RELATED Trusted access: Privacy advocates step up the fight against stalkerware
Aimé developed the tool after a meeting about stalkerware with a women’s shelter in France.
“TinyCheck is quite simple in technical terms,” Aimé told The Daily Swig in a recent interview.
“It is a bridge between your smartphone and the network router. It analyses communications from the phone to look for anything malicious, such as stalkerware.”
 TinyCheck can be used to detect signs of stalkerware on a victim’s mobile device
TinyCheck can be used to detect signs of stalkerware on a victim’s mobile device
Ghosts on the wire
The TinyCheck tool uses heuristics and anomaly detection, including detecting HTTP requests to servers without a registered domain, free SSL certificates, or known malicious domains.
Aimé designed the tool so that it works without having to install anti-stalkerware apps directly on users’ phones or carry out complex forensics.
Read more of the latest data privacy news
According to Aimé, stalkerware is a growing problem: a perpetrator can install freely available malware on a handset with just a few clicks, and the victim is highly unlikely to spot it.
Stalkerware apps even use WiFi rather than 3G or 4G connections, Aimé said, to avoid triggering alerts for excess data usage.
The scourge of stalkerware
In addition to individual users, the developers say TinyCheck could also be helpful to NGOs and human rights organizations.
Law enforcement agencies could also use the tool to gather evidence that a perpetrator had compromised a victim’s phone.
Unfortunately, though, there is no easy way to remove or prevent stalkerware.
Aimé warned that removing stalkerware apps can trigger an alert to those monitoring the handset.
Domestic abuse victims might need to use a different handset, at least until they are safe. TinyCheck itself, however, will only gather only data it needs to operate watchlists associated with indicators of compromise.
Secure development
“A glance at the source code suggests it behaves as described; the only web calls are to check for connectivity and download IOCs, there is no obvious code to report back,” security consultant Gary Hawkins told The Daily Swig.
“It does not appear to contain any SSL/TLS intercept capabilities, so any eavesdropping on someone else’s comms would be limited to metadata and insecure traffic.”
TinyCheck developer Aimé stresses the tool should only be used with users’ consent. And, he warned, although the device can find stalkerware, it unfortunately can’t prevent it.
According to the researcher, users should not rely on phones’ in-built biometric authentication, and should set strong passwords.
“Our advice is [also] to protect your phone and keep it on you at all times,” he said.
More details, including the source code for TinyCheck, is available on GitHub.
READ MORE Security vendors seek to tackle growing stalkerware threat






