Dastardly
Integrating Dastardly with TeamCity
-
Last updated: October 1, 2024
-
Read time: 3 Minutes
You can integrate Dastardly with TeamCity. This enables you to run Dastardly web vulnerability scans as a stage in your existing CI/CD pipeline.
This page contains instructions on how to integrate Dastardly with a simple (example) TeamCity CI/CD pipeline. These instructions have been tested with TeamCity 2022.04.4.
TeamCity agent requirements
Your TeamCity agent must have Docker configured to run containers.
No plugins beyond the TeamCity defaults are required to run Dastardly in a TeamCity CI/CD pipeline.
For information on the machine specification required to run Dastardly scans, see the Dastardly system requirements.
Creating the settings file
Configure access from TeamCity to the repository where your
settings.ktsfile is stored.-
Add the following content to your
settings.ktsfile:import jetbrains.buildServer.configs.kotlin.* import jetbrains.buildServer.configs.kotlin.buildSteps.ScriptBuildStep import jetbrains.buildServer.configs.kotlin.buildSteps.script version = "2022.04" project { description = "Contains all other projects" buildType(DastardlyScan) } object DastardlyScan : BuildType({ name = "Dastardly from Burp Suite Scan" vcs { cleanCheckout = true } features { feature { type = "xml-report-plugin" param("xmlReportParsing.reportType", "junit") param("xmlReportParsing.reportDirs", "+:**/reports/**.xml") } } steps { script { name = "Dastardly from Burp Suite Scan" dockerImage = "public.ecr.aws/portswigger/dastardly:latest" dockerPull = true dockerImagePlatform = ScriptBuildStep.ImagePlatform.Linux dockerRunParameters = """ -e BURP_START_URL=https://ginandjuice.shop/ -e BURP_REPORT_FILE_PATH=%teamcity.build.checkoutDir%/reports/dastardly-report.xml """.trimIndent() scriptContent = """ mkdir -p %system.teamcity.build.workingDir%/reports docker-entrypoint.sh dastardly """.trimIndent() } } artifactRules = """ reports/** => reports """.trimIndent() })
Note
You can set BURP_START_URL to a seed URL for any application you want to scan.
In this example, BURP_START_URL is set to https://ginandjuice.shop/ - this is a deliberately vulnerable web application designed for testing web vulnerability scanners.
The next time your pipeline runs, Dastardly will scan the application you have set under BURP_START_URL.
Configuring the TeamCity pipeline
-
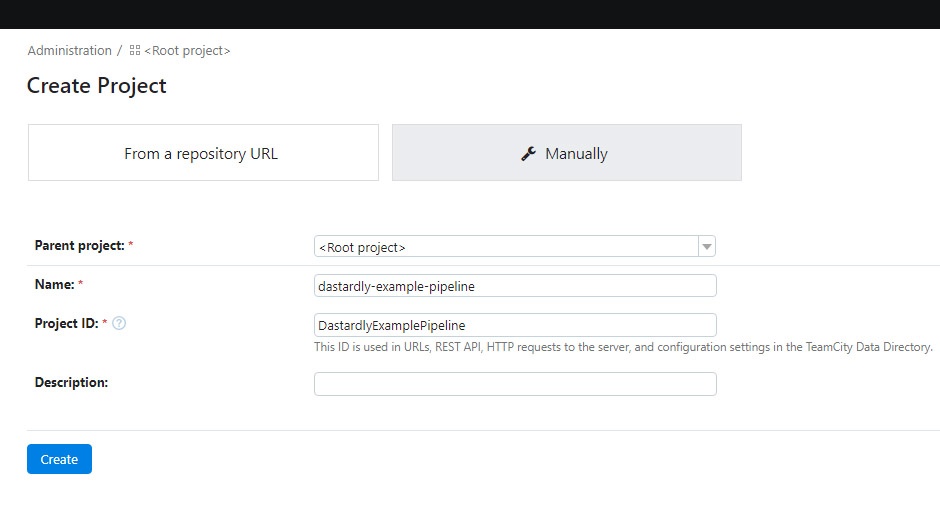
From the main TeamCity interface, click New project... and choose an appropriate place in your project hierarchy.
-
Ensure that Manually is selected.
-
Give your project a Name. You can also add a Description.
-
Click Create.
-
Click Versioned Settings.
-
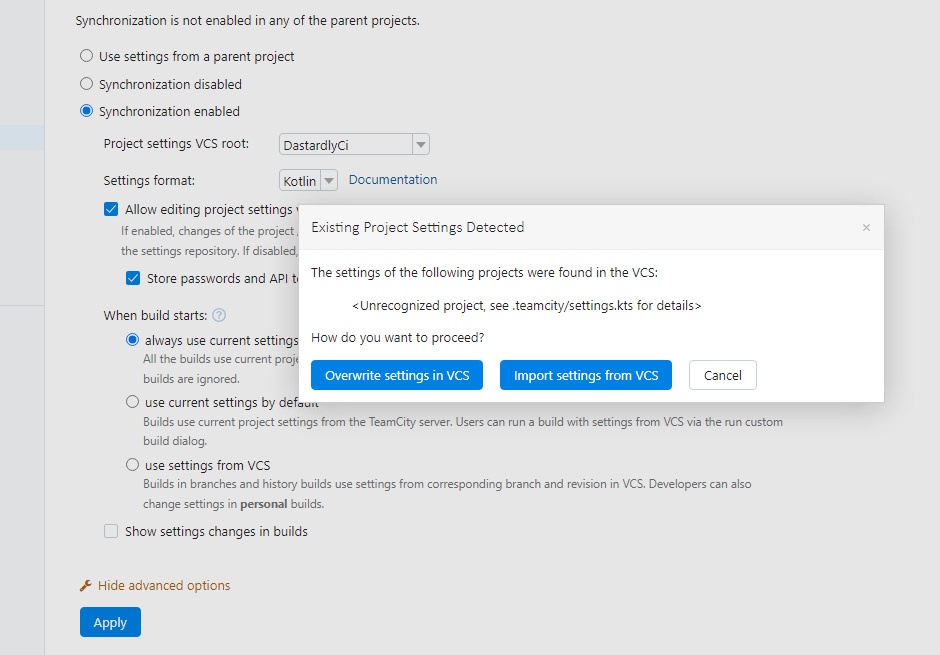
Select Synchronization enabled.
-
Under Project settings VCS Root, click Create VCS root or use an existing option from the Project Settings VCS root drop-down.
-
Ensure Settings format is set to Kotlin.
-
Click Apply.
-
From the Existing Project Settings Detected pop-up, click Import settings from VCS.
Viewing Dastardly scan results in TeamCity
-
Run your TeamCity project containing Dastardly, and allow the scan to complete. Scans run for a maximum of ten minutes.
-
From the main TeamCity interface, click on your project containing Dastardly.
-
Under Dastardly from Burp Suite Scan, click on the build containing your scan.
-
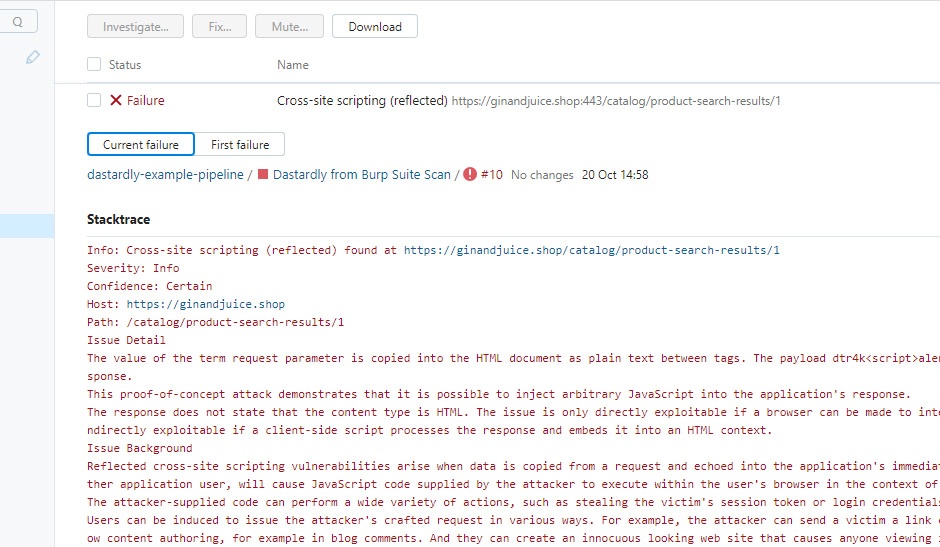
Click Tests. Here you can see any failed tests. See more details of a failed test by clicking on it.
Remediation advice
You can see remediation advice for security issues that Dastardly finds under Stacktrace. This includes links to relevant sections of the free Web Security Academy resource, which provide further detail on web security vulnerabilities.
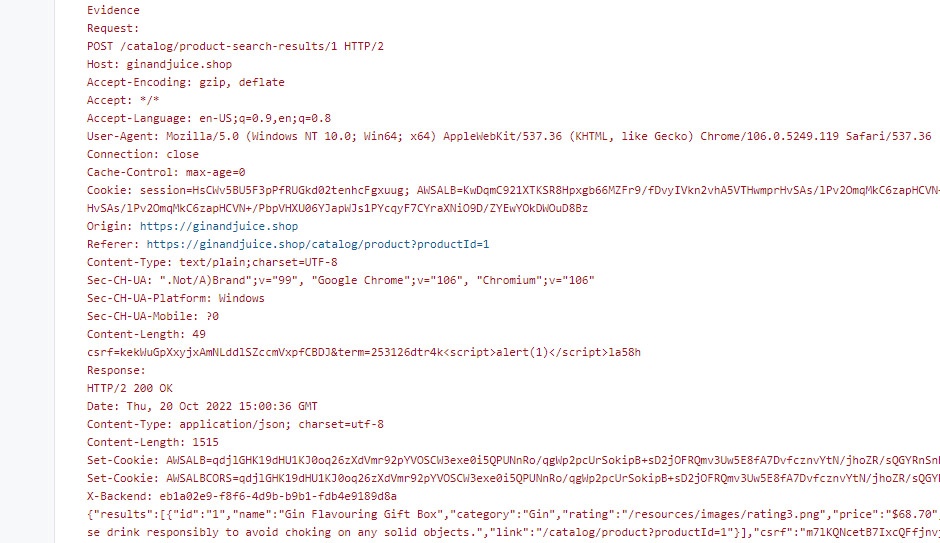
Evidence
You can see evidence for security issues that Dastardly finds under Stacktrace. This evidence includes the request sent by Dastardly to produce the issue, as well as the response sent by the application.